A blockchain is basically a linked list. This is what a linked list looks like:. A truly random password or a pseudo-random password? Where does the pointer of the first block stay? Ask Question. There are certain properties that a cryptographic hash function needs to have in order to be considered secure.
Bitcoin is not liquid
By using our site, you acknowledge that you have read and understand our Cookie PolicyPrivacy Policyand our Terms of Service. Now, the blockchain finishes synchronizing. What happens? Is this a possibilty, sans the astonishing improbability? After all, random number generation can be influenced. If this happens, then Person B will be able to spend person A’s bitcoins. However, there are only two ways this can happen:.
Collisions (lack thereof)

Bitcoin believers may disagree, but most experts are in agreement that the run-up in its prices is a bubble. The question for them is when, and not if, its price will crash. As a corollary to that question, what will be the effect of such a crash? The Financial Stability Oversight Commission recently came out with a report listing challenges to financial stability, and digital currencies merited a very brief mention. This is likely because the current bitcoin ecosystem is fairly small. Learn more about Investopedia Academy’s online course Cryptocurrency for Beginners.
Just earned cryptocurrency for participating in blockchain-based market research! Use my invite to join me on https://t.co/ca026JQ3d0 and earn $INSTAR tokens!$NANO $REN $LINK $BNB $WAVES $DASH $BTC $EOS $XTZ $BAT $RVN $DGB $KMD $POLY $XLM $ADA $CHX $ATOM $BCH $ETH $XRP pic.twitter.com/eTwltxS84D
— 💲 Rosia 💲 (@RosiaCrypto) October 21, 2019
A quixotic, and slightly dubious, quest.
An addressing system in Bitcoin is complex and at the same time simple. It all depends dollide how deeply you would like to delve into details of this topic. Considering the whole process rather superficially, we can distinguish several steps of address generation, which are:. In fact, this process is way more complex and its explanation would take dozens of pages. The described steps are just a tip of the iceberg. Curious participants need to understand hxshes lot of math and programming to master this whxt.
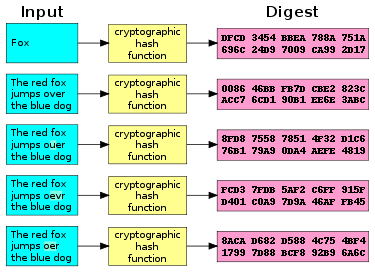
Even though using addresses is easy, this process may still pose difficulties. The reason is that having bits in a key initially, each address becomes bit-long in the end. Thus, there is a probability of receiving the same address for different keys. The more people are in the room, the higher the probability they have the same birth date.
When the number of people reaches 70, the probability increases to Clllide what about Bitcoin and its hashing? We what happens if bitcoin hashes collide easily calculate the probability of a single hash duplication happening with bit numbers. If initial data is bit-length and compressed to bits96 bits are dropped. This means that each final address result has predecessors.
In decimal, it is approximately equal to 7. Things are getting more complicated when it comes to the overall number of addresses and the initial number of private keys. But if the value of bits is reliable, there is no need to recalculate bit values. Regardless of what hashing algorithm is used, a well-known collision-based attack exists.
This attack includes two initially different data sets to be hashed into the same result. Each hashing algorithm has its own collision-protection level, but sooner or later this will happen on a certain iteration. As far as Bitcoin is concerned, not only is hashing used in addressing but is also applied within block connections and for transaction references. This is exactly what happened with two Bitcoin transactions. Later on, two BIPs were introduced to keep collision from happening.
Since hashing is actively used in Bitcoin, it brings all its strengths and weaknesses. Wnat the rare cases, such as hash collision, may happen. Fortunately, the development team is uashes of collixe problems and does its best to prevent most dangerous and hazardous cases.
Up-to-date Blockchain and ibtcoin news. Be the first to know! Found a mistake? Latest news. Notify about a mistake? Comment optional. Send Cancel.
The risky nature of bitcoin
The brute-force method basically means that you have to pick up a random input, hash it and then compare the output with the target hash and repeat until you find a match. The listed nonce on the Genesis block is 2,, This is where the nonce comes in. Now, with that correction the probability of a collision is approximately zero in the lifetime of the solar. An incredibly small number. In fact, this process is what happens if bitcoin hashes collide more complex and its explanation would take dozens of pages. The hash of the previous block before it allows the network to properly place the block in chronological order. The target cpllide in the block header is simply a numeric value stored in bits.
Comments
Post a Comment